Application Support
Windows 7 Registry
Registry Security
- The registry database is protected by its own security system. Each key is assigned permissions, an owner, and optionally a list of users to audit when the key is accessed. To see the permission settings on a key, use the graphical registry editor tool, REGEDIT.EXE. The permissions window is representative of what is shown when the permissions on a key are initially opened. Access to a registry key and the values it contains can be explicitly allowed or denied based on the user or the groups they belong to.
- The basic permissions usually do not reveal all of the fine security details that exist in the registry database. By clicking on the Advanced button in the standard registry permissions window, the advanced permissions window is opened.
- Locate and select the key in the left pane.
- Right-click it and select Permissions.
- Select the Users entry in the top Group or User Names section. If Users is not listed, click Add, type Users, and click OK.
- In the lower section, check Full Control and then click Apply. If this is successful, click OK.
- If you are unable to make the changes even though you're running the Registry Editor as an Administrator, click Advanced and select the Owner tab.
- If the Current Owner is listed as unknown, select Administrators in the lower list and click OK.
- Click OK to close the Advanced Security Settings dialog box, and return to Step 3.
- Security settings are inherited from the top of the hive down to the bottom of the hive. Note that the option exists to disable permissions inherited from parent keys and to force permission settings down to child keys in the hive. Permission inheritance and default security options should not be changed without a good reason to do so. Many of the predefined security settings include special permissions that cannot be changed without negatively impacting the computer's stability and ability to run. Permissions are not exported with registry data; they can only be preserved with a full backup that preserves the system state.
- The owner of the keys is usually listed as SYSTEM - the operating system itself. This allows the operating system to modify permissions regardless of what permissions are explicitly defined on the registry keys. This can be changed to an administrative user or the built-in Administrators group, but this can also have a severe negative impact on the computer's stability and ability to run.
- In Windows 7 the operating system code and services run in a user session that is not shared with any user accessible interfaces. If registry permissions are altered to restrict access or operations to users only, the registry data may not be available to the operating system at all. This will probably result in a nonbooting computer that requires a complete restore from backup.
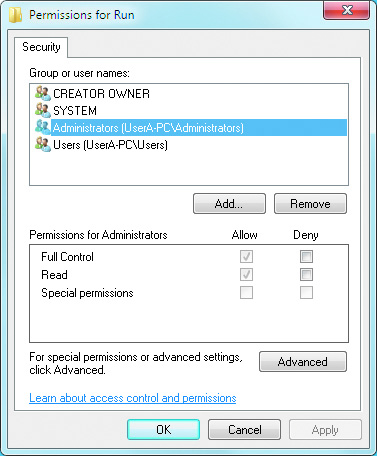
Just as files and folders in an NTFS-formatted disk partition have security attributes to control access based on user and group identity, Registry keys and values also have a complete set of Access Control attributes that determine who has rights to read, write, and modify each entry. If you absolutely must change permissions or auditing controls, locate the desired key or value, right-click it, and select Permissions.
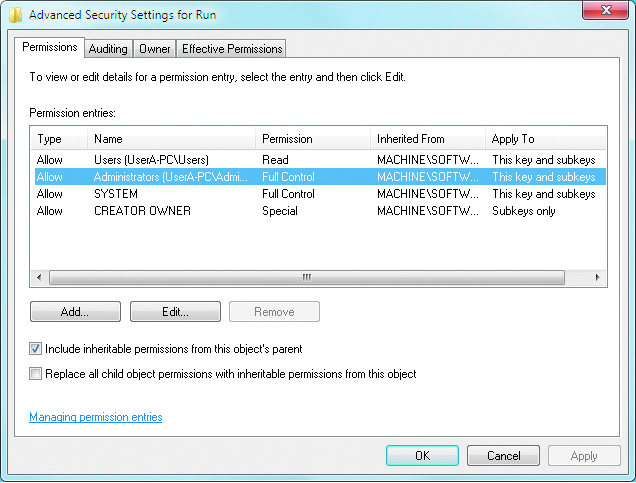
To set more generous permissions, follow these steps: