Intalling Windows 7
Attended Installation
- An attended installation requires you to manually start and perform the installation. You start the installation by running Setup.exe.
- The process for performing an attended installation is much improved over Windows XP. Windows 7 minimizes user involvement during installation. You enter information only at the very beginning and very end of the installation.
Product Activation
- It is a process put in place by Microsoft to reduce piracy. If an installation of Windows 7 is not activated within 30 days, Windows 7 displays a Windows Activation dialog box that reminds the user to activate Windows 7. The desktop background is also changed to solid black. However, Windows 7 functionality is not impaired.
- You can activate Windows 7 from the System applet in Control Panel.
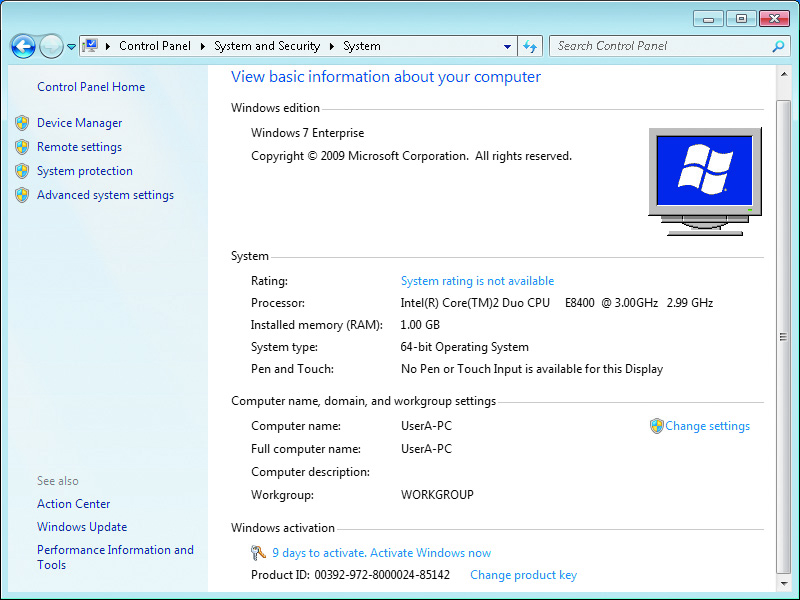
- The product key used during installation is associated with the specific computer that is performing the activation. If you perform significant hardware changes to your computer, you may be forced to reactivate Windows 7.
- The volume license agreement allows for two types of keys:
- Multiple Activation Key (MAK). There are two ways to activate computers using a MAK:
- MAK Independent activation: MAK Independent activation requires that each com-puter independently connect and be activated with Microsoft, either over the Internet or by telephone. MAK Independent activation is best suited for computers within an organization that do not maintain a connection to the corporate network.
- MAK Proxy activation: MAK Proxy activation enables a centralized activation request on behalf of multiple computers with one connection to Microsoft. MAK Proxy activation is configured using the Volume Activation Management Tool (VAMT).
- Key Management Service (KMS)
- KMS activates computers on a local network, eliminating the need for individual computers to connect to Microsoft. To do this, KMS uses a client-server topology. KMS clients can locate KMS hosts by using Domain Name System (DNS) or a static configuration. KMS clients con-tact the KMS host by using Remote Procedure Call (RPC).
- The network must meet or exceed the activation threshold (the minimum number of qualifying computers that KMS requires).
- KMS can activate both physical computers and virtual machines (VMs). To qualify for KMS activation, a network must have a minimum number of qualifying computers, called the activation threshold. KMS hosts activate clients only after meeting this threshold. To ensure that the activation threshold is met, a KMS host counts the number of computers requesting activation on the network.
- KMS activation requires Transmission Control Protocol/Internet Protocol (TCP/IP) connectivity. By default, KMS hosts and clients use DNS to publish and find the KMS. The default settings can be used, which require little to no administrative action, or KMS hosts and clients can be configured manually based on network configuration and security requirements.