Managing File Systems
Supported File System
New Technology File System (NTFS)
The New Technology File System (NTFS) was first introduced with Windows NT and is supported by Windows 7. NTFS was introduced as a secure and efficient file system that is commonly used in business computing environments. Several operating systems introduced after Windows NT include support for earlier versions of NTFS including Windows 2000, Windows XP, and Windows Vista. MS-DOS, Windows 3.x, and Windows 95/98/ME do not support the NTFS file system.
NTFS partitions are theoretically limited to 256 TB, but the practical limit is lower. Basic disks using the old IBM standard for partitions are restricted to 2 TB. Newer dynamic disk partitions are limited to 16 TB.
NTFS stores files and folders in a way that looks very similar to the FAT file system. The difference is in how that data is secured, reliably managed, and allowed to grow. NTFS supports partition sizes above the 32 GB limit imposed on FAT32.
NTFS offers comprehensive folder- and file-level security. This allows the setting of an additional level of security for users who access the files and folders locally or through the network. For example, two users who share the same Windows 7 computer can be assigned different NTFS permissions, so that one user has access to a folder but the other user is denied access to that folder.
NTFS also offers disk management features-such as compression and encryption services-and data recovery features. Windows 7, Windows Vista, Windows XP, Windows Server 2003, and Windows Server 2008 use NTFS 3.1 include the following features:
- When files are read or written to a disk, they can be automatically encrypted and decrypted.
- Reparse points are used with mount points to redirect data as it is written or read from a folder to another volume or physical disk.
- There is support for sparse files, which are used by programs that create large files but allocate disk space only as needed.
- Remote storage allows you to extend your disk space by making removable media (for example, external tapes) more accessible.
- You can use recovery logging on NTFS metadata, which is used for data recovery when a power failure or system problem occurs.
The advantages of using NTFS includes:
- Log file and checkpoint consistency checks: NTFS uses an advanced system to incrementally update the directory information about files and folders stored on the NTFS partition. Information about files and folders stored on the disk is kept in a special fle called the Master File Table (MFT), which is named $MFT on the disk. The MFT is the most important NTFS system file because it is a relational database that provides the starting point for accessing any file on the NTFS partition.
- Automatic bad cluster management: An NTFS system file called the Bad Cluster File keeps a record of all the clusters that are considered unusable by the file system within that volume. When the operating system detects that a cluster cannot be trusted to store data, the cluster's identification will be automatically added to this file. If the bad cluster is currently used by a file or folder to store data, the operating system will try to move that data to a different cluster. The move is transparent to the user and does not require user intervention.
- Transactional NTFS: It is used to protect file data. Updates using a transactional system utilize change logs and checkpoints to validate that updates have successfully completed. If there is a problem with the updates to a file, the changes can be replayed or rolled back to a known good state.
- File names stored in Unicode and 8.3 DOS format: Files and folders can use Unicode chracters in the file name. Each file has two names assigned to it, a long file name and an 8.3 file name compatible with MS-DOS. The long file name is limited to 255 characters and can contain any valid Unicode character. The 8.3 DOS name contains a maximum of eight characters followed by a period and a maximum of three characters that act as the file extension.
- Alternate data streams: A file can have multiple streams of data associated with it. Each stream is a sequence of data bytes.
Every file has one unnamed stream that is used to store the byte data typically associated with the file and visible to users and applications. Files stored on the FAT file system would only have the data associated with the unnamed stream. Applications can create additional named streams and link them to the file in addition to the unnamed stream. This is only visible and useful to the application itself, as the user does not have direct access to the named streams.
Applications create the named streams and refer to them using the file name and the name of the stream to interact with the correct data. The use of the data is determined by the application designer. A common example is a named stream that could be used to store a thumbnail of a large image for quick and easy previews within a graphic application. The file name becomes a pointer to multiple related data streams instead of just one.
- Encrypted File System (EFS): A file can have its contents encrypted to protect the information from unauthorized users.
Even though a user obtains access, they require additional security information to decrypt and access the file's contents. The Encrypting File System (EFS) is the part of the operating system that handles these operations. EFS is a valuable form of protection for local file access. If a malicious user gains direct access to the hard disk, unencrypted files can be compromised. The user could gain direct access by physically removing the hard disk or booting the computer with a different operating system that allows direct access to the NTFS partition. With EFS encryption enabled for a file, the malicious user would not be able to decrypt the data they have access to. EFS is a local-access protection tool; when an encrypted file is sent across the network or in an e-mail, it is sent in its unencrypted form.
Digital encryption keys from each user are implemented to encrypt and decrypt the file's contents. Without the correct key the file's contents are inaccessible. Even an administrator with full permissions to the file will not have access unless their encryption key is one of the recog- nized accounts.
Files that are encrypted with EFS will stay encrypted until an authorized user disables encryp- tion on the file or copies the unencrypted contents to a storage device that does not support EFS. - File and folder permissions: Each file and folder has its own list of permissions that determine the actions that users or groups are allowed to perform with that item.
- Compression: Files can be compressed to save space on NTFS volumes. The compression process is transparent to the user and their applications. From the user's perspective, the file takes up its uncompressed amount of space on the disk. When a compressed file is accessed, Windows 7 will decompress the file and present it to the user and their applications. When the file is closed, it is compressed once again. Not all files should be compressed. Each time a file is compressed or uncompressed the CPU performs the calculations required. This impacts the computer's performance to some extent. If many compressed files are being accessed, the impact to performance may be significant.
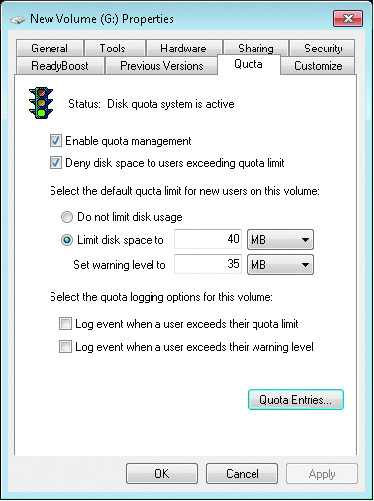
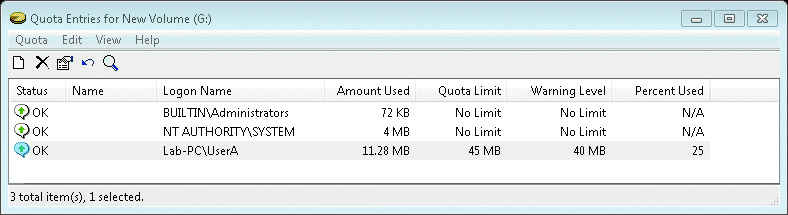
- Disk quotas: The amount of disk space used by a user can be restricted to ensure that one user does not exhaust or monopolize available space in an NTFS partition.
The amount of disk space used by a user can be restricted to ensure that one user does not exhaust or monopolize available space in an NTFS partition. By default, disk quota limits are not enabled for NTFS partitions.
Once disk quotas are enabled for a partition, the operating system tallies the amount of disk space used by each unique owner listed for all files on the volume. The first time quota management is turned on, the system will take some time to identify all the owners and count up all the file sizes attributed to each owner. - Shrinkable/extendable partitions and volumes: If a partition or volume is formatted with NTFS, the file system can adapt when the partition or volume is resized.
- Volume mount points: They allow an empty folder in an NTFS-formatted file system to point to another partition or volume in the local computer.
The partition connected via the volume mount point can be formatted with FAT, FAT32, or NTFS. Note that the FAT option in the new volume wizard refers to the FAT16 file system. The disk space reported for the NTFS volume hosting the mount point does not increase; the volume mount point is just a pointer. The free space and control of the target pointed at by the volume mount point is separately reported and managed.
Activity 5-2
- Symbolic links: A symbolic link is stored in the directory of a folder as a file system object. The purpose of a symbolic link is to point to a file or folder located somewhere other than that folder.
A symbolic link can point to a file or folder on the local computer or to a remote location identified with a UNC path. If the target is remote, then the other computer hosting the target must also support symbolic links. There are two special types of symbolic links known as hard links and junction points.
Windows 7's support for symbolic links includes a special type of symbolic link called a hard link. A hard link can only point to a f le on the same partition or volume as the hard link object. Hard links cannot be used with folders.
A regular symbolic link points to the directory or directory entry of a target in its target loca- tion. A hard link is a duplicate directory entry that points to the contents of a target file. When a user or application accesses a hard link, they believe the file content exists in the folder holding the hard link.
A junction point is a special type of symbolic link that points to folders only. The path to the target folder must be specified using an absolute path. The absolute path points to a target that can be located without needing to know the location of the original junction point object. Vol- ume mount points are an example of how Windows 7 can use junction points. Junction points are also used by Windows 7 to organize content in user profile folders. - Sparse files: A file can be stored with a special attribute to mark it as a sparse file. Large portions of a sparse file contain bytes with the value of zero.
Instead of storing long strings of zeros, the sparse attribute tells NTFS to track the ranges of empty data. The sparse file will then contain nonzero data and a list that identifies where ranges of empty data occur between the nonzero data.
If a sparse file contains 50 MB of nonzero data and 200 MB of zero data, the file size will be just over 50 MB with the sparse attribute set. The same file copied to a FAT partition would require 250 MB of disk space.
Activity 5-1