Windows 7 Security Features
Data Security
Encryption Algorithms
- Encryption is the process of taking data and making it unreadable. Decryption makes data readable again.
- Symmetric encryption uses the same key to encrypt data and decrypt data. The key is a long number that is very hard to guess.
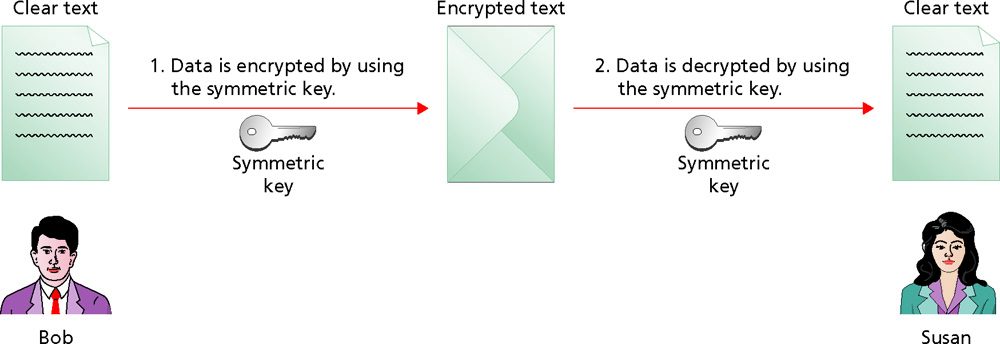
- Since symmetric encryption is strong and fast, it is well-suited to encrypting large volumes of data such as files. It is used by both EFS and BitLocker Drive Encryption.
- The biggest problem with symmetric encryption is securing the key.
Read more about symmetric encryption at:
http://www.howstuffworks.com/encryption2.htm.
- Asymmetric encryption uses two keys to encrypt and decrypt data. Data encrypted by one key is decrypted by the other.
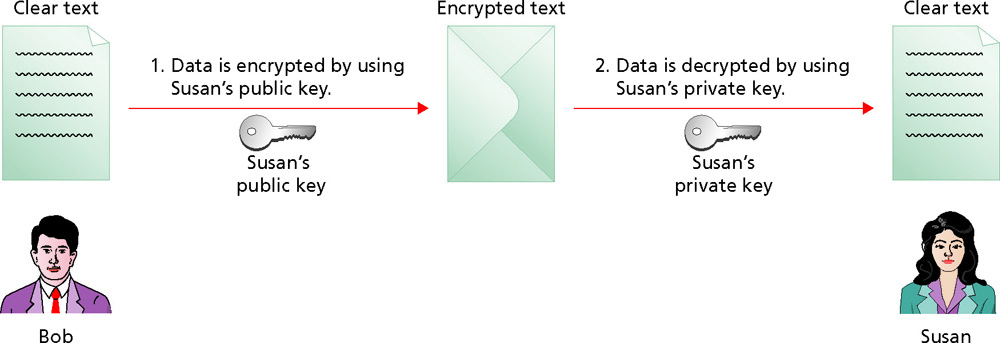
- The keys are part of a digital certificate. Digital certificates are obtained from certificate authorities.
- Asymmetric encryption requires more processing power and is less secure than symmetric encryption.
- Many systems that require encryption use symmetric encryption to encrypt the data and then use asymmetric encryption to protect just the symmetric key.
Read more about asymmetric encryption at:
http://computer.howstuffworks.com/encryption3.htm.
- Hash encryption as a one-way encryption, which means that it encrypts data, but the data cannot be decrypted. Hash encryption is used to uniquely identify data rather than prevent access to data.
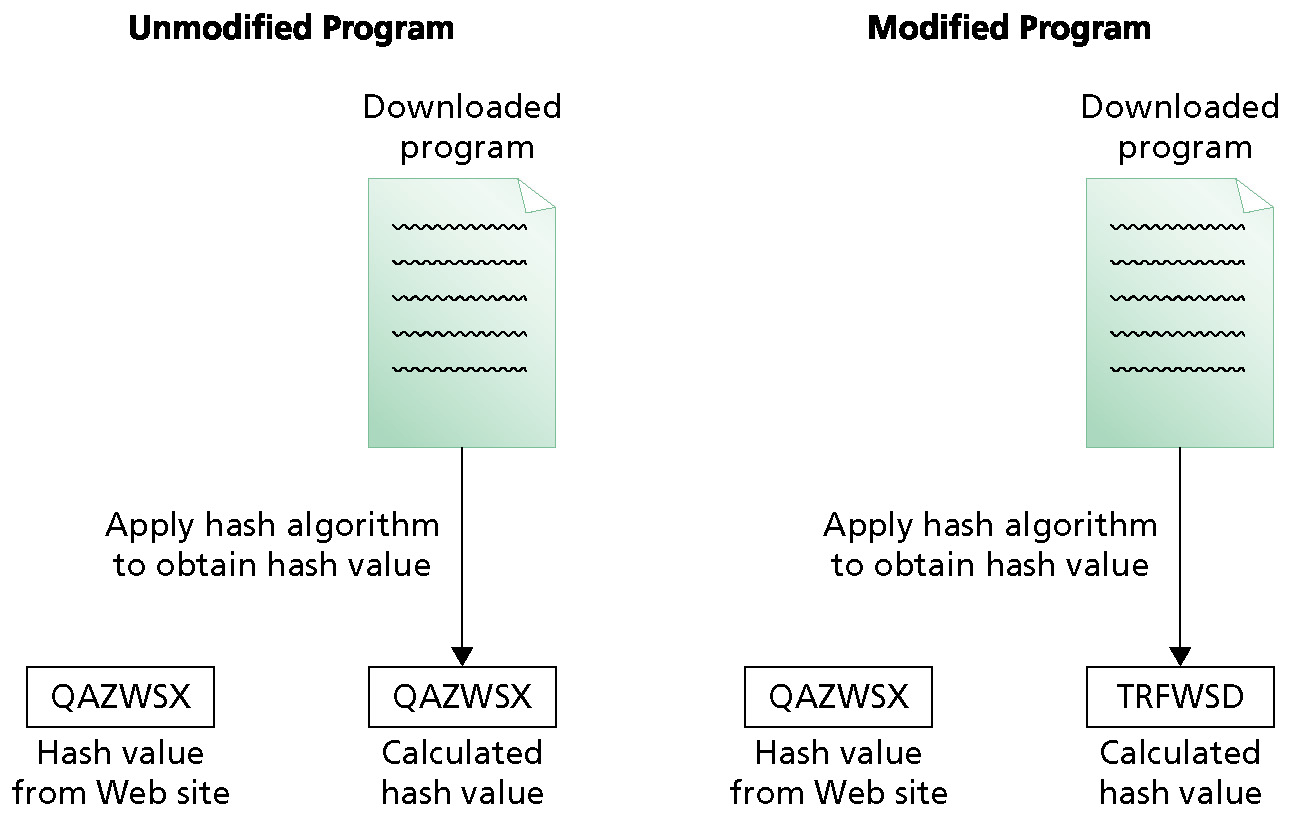
- Sometimes hash values for data are referred to as fingerprints.
- Hash encryption is used for storing passwords. When passwords are stored as only a hash value, it is impossible to decrypt the password.
Read more about hash encryption at:
http://computer.howstuffworks.com/encryption5.htm.


