Networking
Windows Firewall
Advanced Firewall Configuration
To access Windows Firewall with Advanced Security, click Start => Control Panel => Large Icons View => Windows Firewall and then click the Advanced Settings link.
- Advanced Firewall Configuration allows you to configure more complex rules, outgoing filtering, and IPsec rules.
- The tools available to perform advanced firewall configuration are:
- Windows Firewall with Advanced Security utility: This utility is a graphical tool to configure all of the Windows Firewall features on a single computer.
- Configure firewall properties
- View and edit rules
- Create new firewall rules
- Create new computer connection security rules
- Monitor Windows Firewall rules and connections
- Netsh: This is a command-line utility for managing network configuration. It is also capable of configuring allof the Windows firewall features on the local computer.
- Group Policy: To quickly and easily manage the Windows Firewall settings in a corporate environment, you should use Group Policy. It \allows firewall settings to be applied to hundreds or thousands of computers very quickly.
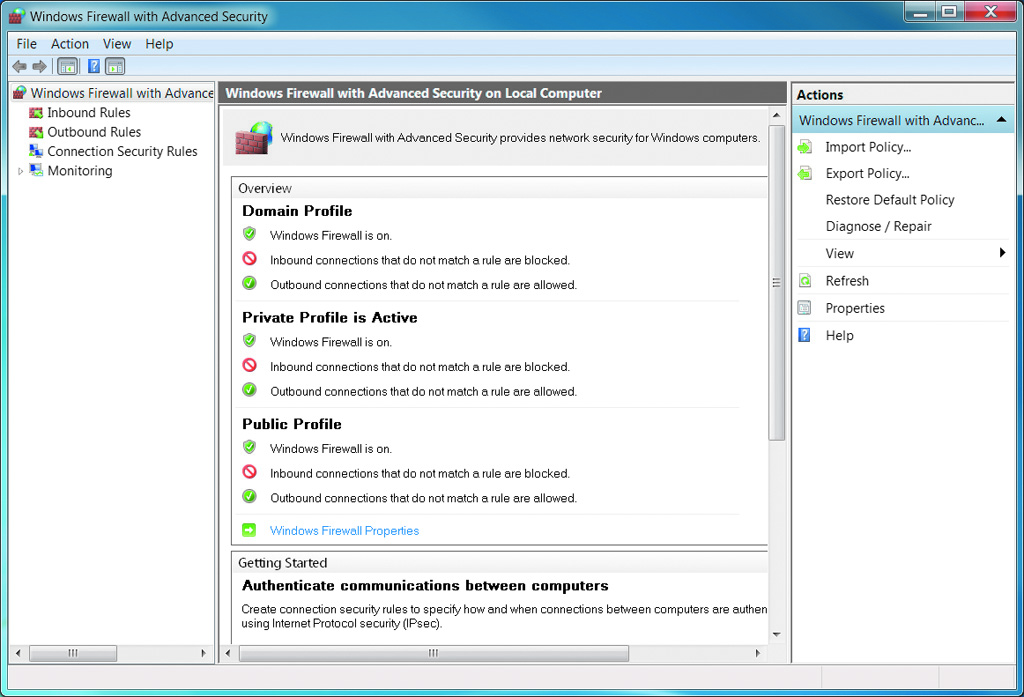
- Windows 7 stores the firewall properties based on location types. The configuration of each location type is referred to as a profile.
- TheWindows Firewall with Advanced Security on Local Computer node shows the configuration of each profile.
- Enable or disable Windows Firewall
- Configure inbound connections
- Block (default): All inbound connections are blocked unless specifically allowed by a rule.
- Block all connections: All inbound connections are blocked regardless of the rules.
- Allow: All inbound connections are allowed unless specifically blocked by a rule.
- Configure outbound connections
- Allow (default): All outbound connections are allowed unless specifically blocked by a rule.
- Block: All outbound connections are blocked unless specifically allowed by a rule.
- Customize protected network connections: Select which network interfaces this firewall state applies to - All are selected by default.
- Customize settings
- Display notifications to the user when a program is blocked from receiving inbound connections.
- Allow unicast response to multicast or boadcast network traffic.
- Apply local firewall rules.
- Apply local connection security rules.
- Customize logging
- Name
- Size limit
- Log dropped packets
- Log successful connections
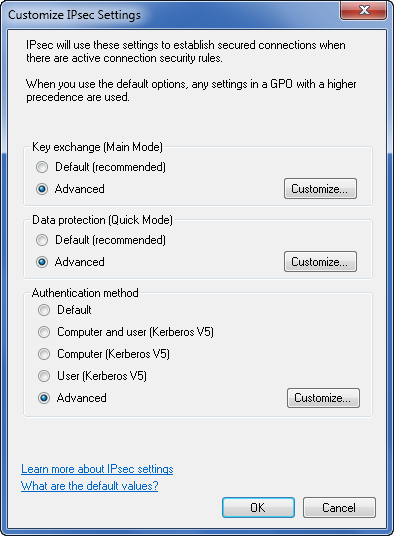
- IPsec is a system for securing and authenticating IP-based network connections.
- The IPsec settings you can configure are:
- Key exchange
- Data protection
- Authentication Method
- A large number of inbound and outbound rules are created by default in Windows 7.
- You modify an existing rule by opening its properties. Tabs in the properties of an outbound rule include:
- General
- Programs and Services
- Computers
- Protocols and Ports
- Scope
- Advanced
- You can create new firewall rules using a wizard.
- The rule types you can create with the Outbound Rule Wizard are:
- Program
- Port
- Predefined
- Custom
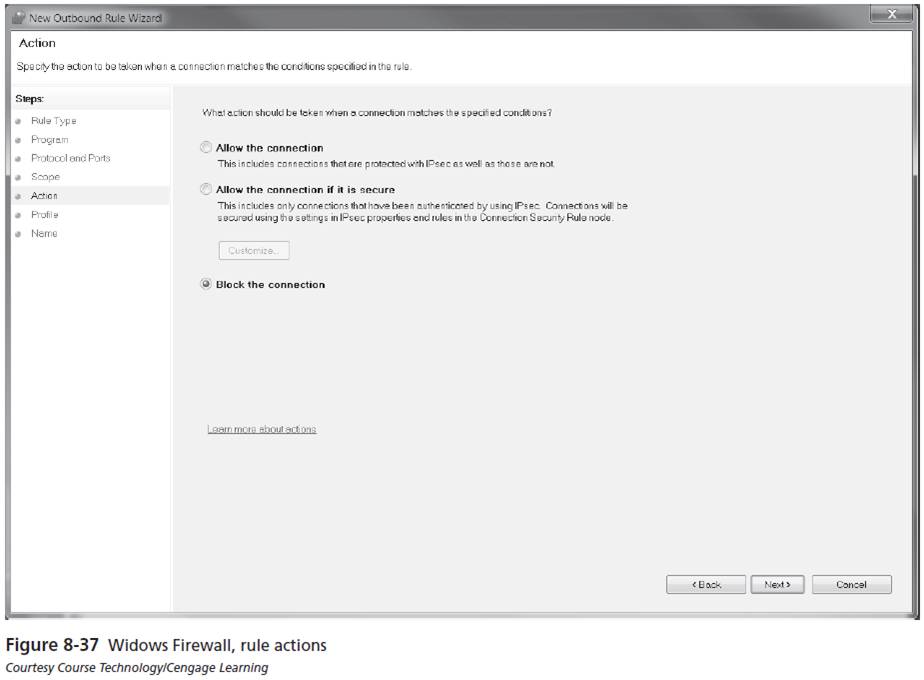
- Allow the connection
- Allow the connection if it is secure
- Block the connection
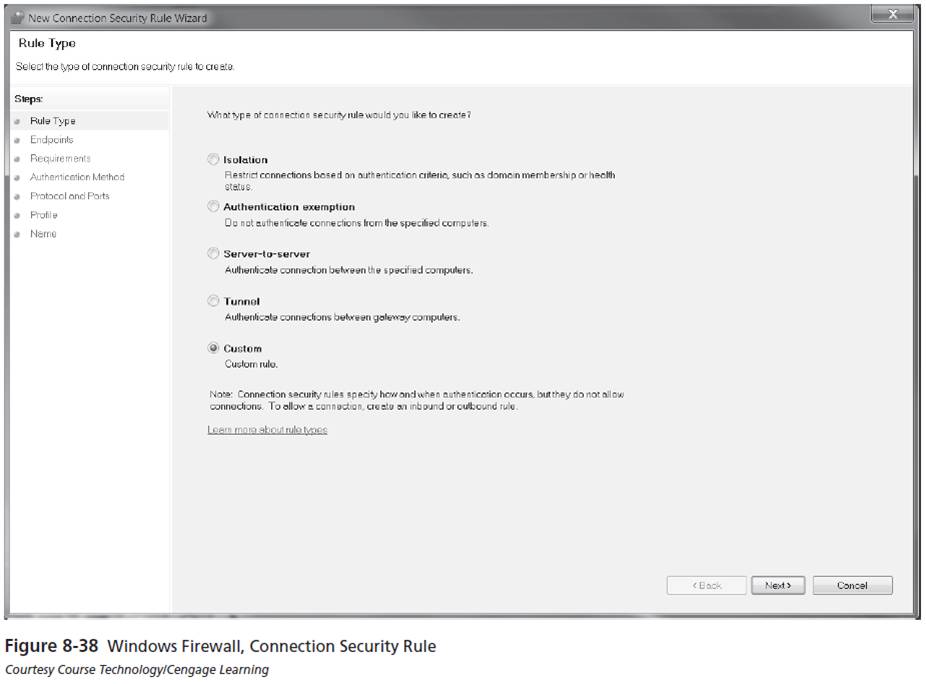
- You can use IPsec to authenticate and secure communication between two computers.
- Isolation
- Authentication exemption
- Server-to-server
- Tunnel
- Custom
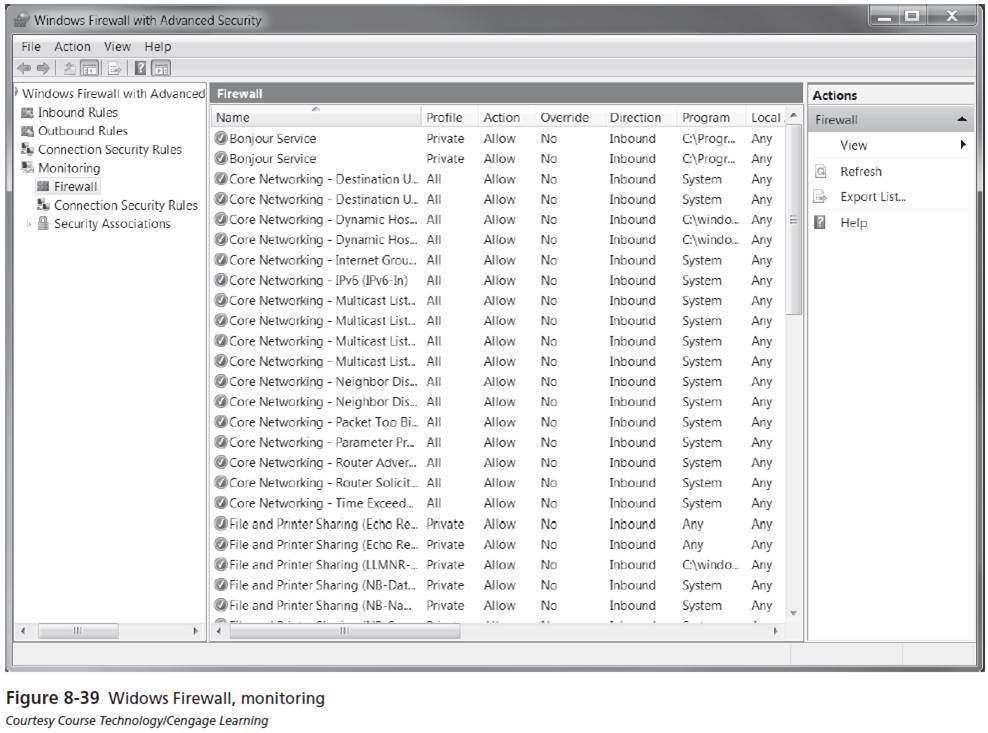
- The Firewall node under Monitoring in the Windows Firewall with Advanced Security snap-in allows you to see all of the rules that are enabled in one screen.
- The Connection Security node under Monitoring allows you to see the computer connection security rules that are enabled and any security associations that are active.
- Security association is the set of rules for communication negotiated between two computers. If two computers have a security association, they are using IPsec to communicate. Security associations are listed in two categories:
- Main mode: Used for the initial configuration of an IPsec connection, including authentication.
- Quick Mode: Signifies a secure IPsec communication channel has been negotiated.
By using this interface, you can:

In each profile, you can:
Read more about IPsec at:
http://en.wikipedia.org/wiki/IPsec.
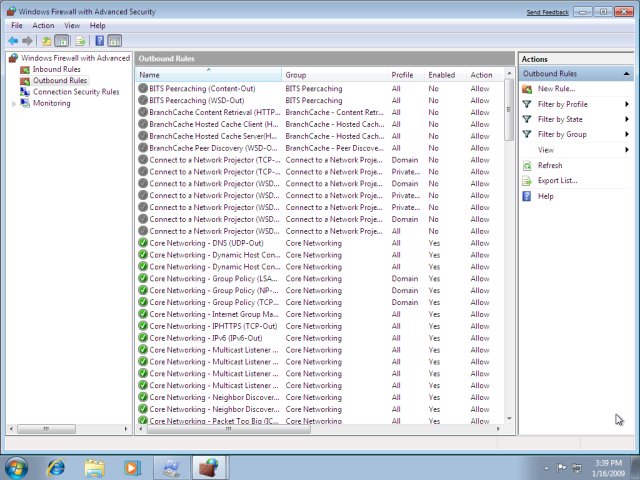
The actions for a rule are:
The security rule types are: